Learn about the underlying structure of the blockchain, and what proof-of-work and proof-of-stake are!
In our previous article, we briefly discussed the blockchain and how it is comprised of a vast network of computer systems that can store any kind of data using a distributed ledger model.
To recap:
- A distributed ledger means that the data is shared between different computers on the network - not just centralized to one point of access, which would make it vulnerable to cybersecurity threats.
- These computers "talk" to each other to verify that they all have the same data, and agree on what seems valid or suspicious in a majority voting process known as consensus.
- If more than 50% of the computers on the network decide that the new data being entered does not make sense with previously existing data - that data is flagged as suspicious and rejected by the entire network. This is one of the underlying mechanisms that makes the blockchain so secure.
- For this reason, a 51/50 attack is required to successfully "hack" the blockchain. In a network of 10,000 computers, you would need to convince at least 5,001 of them that your version of the data is the correct one - no easy feat. Otherwise, the majority of them would reject your version of the data AND tell the other computers to update their data to match the majority.
What is the structure of the blockchain?
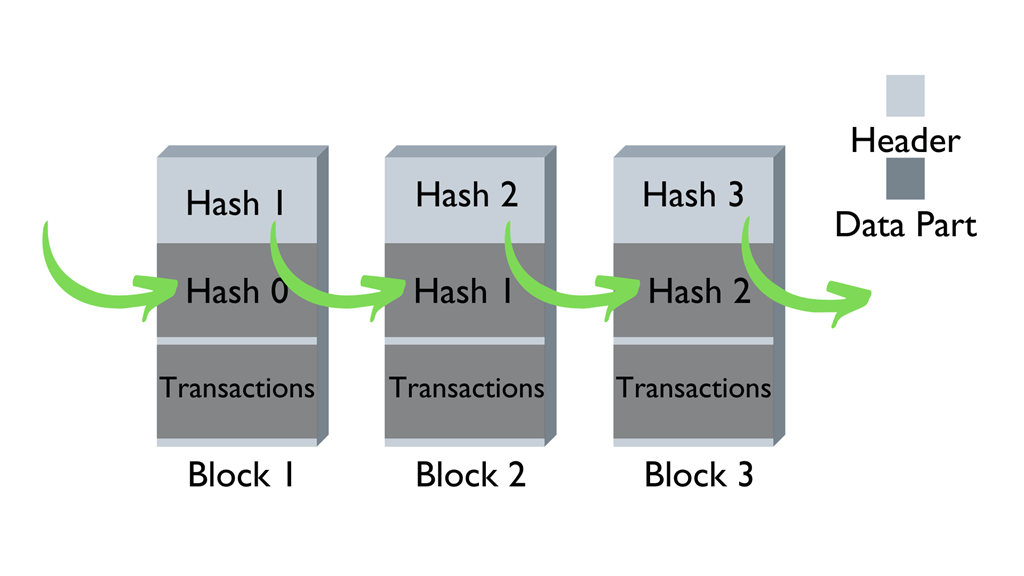
The word "blockchain" was coined because it is literally that - a chain of blocks. To keep things simple, a block is a piece of data with some identifying features added to it that will either allow other blocks to "chain" with it, or be rejected.
To create a block, you must generate a 32-bit number called a nonce, which acts similarly to a key. Every nonce has a corresponding hash it generates.
A hash is a 256-bit number that serves as one of the unique digital signatures for that block. Data (the transaction in this case), nonce, and hash are all sealed together in a block once created - and that block cannot be altered or added to unless the following block references that hash.
So, every block should contain a nonce, the data, and two hashes - one to reference the previous block, and another hash that identifies itself.
How can someone add to/modify the blockchain?
Remember how we said that a block cannot be added to or modified unless the following block has a hash that references it?
Think of that hash as a combination to a safe that can only be generated by a very specific nonce. A nonce is a 32-bit number, while a hash is a 256-bit number. This means that there are over 4 billion possible combinations to try before you can crack the safe.
A miner runs very complex computational programs to generate and test nonces - and only one of these nonces will create the hash that "unlocks" a block. Most of the time, they end up failing and will have to move on. However, if they succeed - they will be rewarded for their work with a small amount of cryptocurrency.
To summarize everything that we have just learned: miners are worker bees that help people add or modify data in the blockchain. Blocks in the blockchain are like a safe that can only be opened with the right combination. And, blocks that don't make sense to at least 50% of the computers on a network will be flagged as suspicious and rejected across the entire network.
What is proof-of-work?
When you apply for a job, that employer will demand your resume and references as proof. In the same way, the blockchain will demand your proof of work before it allows you access to modify or add to a block. This is the third major security feature that the blockchain has - along with consensus and hash keys.
Proof-of-work is evidence that you spent a reasonable amount of time on computations before you unlock a block. The average time it takes to run that many computations is about 10 minutes. That's why every block contains a timestamp when it was created - it would be very suspicious if you were able to "unlock" and add blocks every few seconds!
Not having proof-of-work is grounds for the network to reject your activity. You should also note that tampering with any block on the blockchain will invalidate all following blocks. This is because every block has a hash that references the block before it - and changing the hash in any section of the blockchain would cause the hashes to be incorrect in every resulting block.
So what's this newer “proof-of-stake?”
Proof-of-stake is a consensus mechanism that was developed to counter the extreme energy costs and carbon footprint of mining computers that run proof of work. Calculating 4 billion possible combinations to find the correct hash is no small feat - and it is estimated that Bitcoin miners alone consume more energy in a year than the entirety of Switzerland.
Here's how it works:
- Instead of miners, people who participate in proof-of-stake are called validators. Anyone can be a validator, because this process can happen from their own computer - they don't need insane processing power for this.
- To volunteer as a validator, you must stake a certain amount of a cryptocurrency to qualify. For example, Ethereum requires that you stake at least 32 ETH (their currency) to qualify. Staking means that you agree to set aside an amount of cryptocurrency to be used to support the blockchain network and verify transactions.
- You do NOT lose or move your crypto to a different location when it is staked - you're only giving permission for it to be "put to work." Oftentimes, the condition for staking is that you lock-in those funds - meaning you cannot withdraw it for a set period of time.
- The reward for staking is usually paid as a yield - similar to an interest payment, except you're getting additional amounts of that crypto.
Yield payments are what incentivize validators to join a network, making proof-of-stake networks highly-scalable because millions of people can participate with an ordinary computer instead of a supercomputer built for mining.
How does validation happen?
Once your cryptocurrency has been staked, your computer's processor will be used to verify transactions in one of two ways:
- Creating a new block (adding data to the blockchain)
- Deciding with other validators on the network that a new block looks legitimate
Note that your computer isn't constantly being made to perform these tasks - it is assigned completely at random to validators on the network.
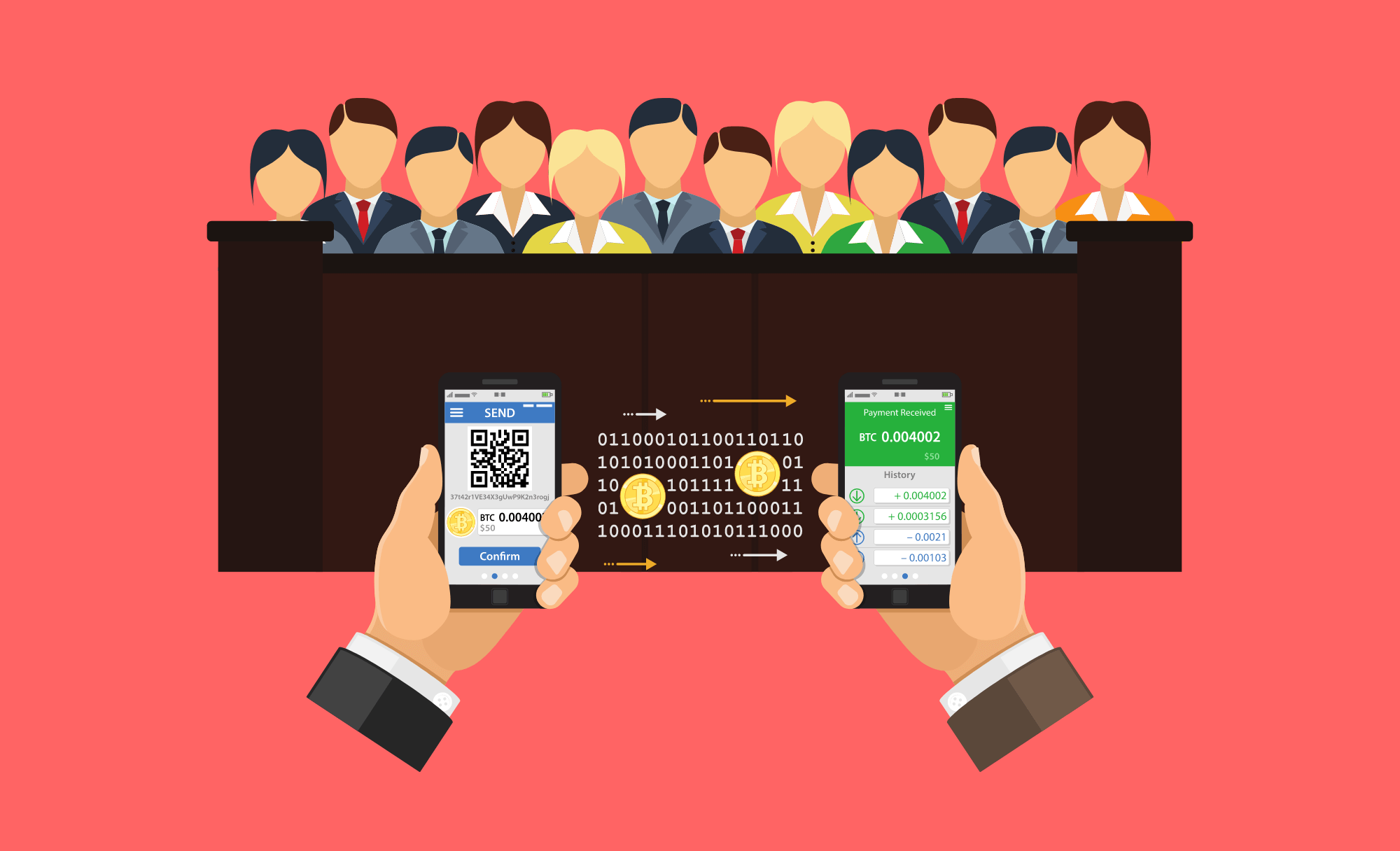
When a new block is being created, a single validator will verify that transaction and add it to a shard block. For the purposes of our illustration, let's say that a shard block is similar to a defendant at trial.
128 other validators will then vote if that defendant looks innocent (legitimate) or guilty (suspicious). This process is known as attestation. If at least 2/3rds of the validators agree that the transaction is valid - the block is closed and added to the blockchain.
The Takeaway:
We know this information is alot to process (no pun intended!). But whether you decide to actively invest in crypto on an exchange, or use a reliable earnings platform like Finblox - it's important to understand the technology behind the cryptocurrencies you purchase, and why your investment is so secure.
Thanks for reading! Please subscribe if you haven't already, and stay tuned for our next article on dApps, and exciting real-world applications of the blockchain!
This content is provided for informational purposes only, and should not be relied upon as legal, business, investment, or tax advice. You should consult your own advisers as to those matters. Charts, graphs and references to any digital assets are for informational and illustrative purposes only.